Service tokens
You can provide automated systems with service tokens to authenticate against Cloudflare’s Zero Trust policies. Cloudflare for teams will generate service tokens that consist of an ID and Secret. Automated systems or applications can then use these values to reach an application protected by Access.
This section covers how to create, renew, and revoke a service token.
Create a service token
-
On the Zero Trust dashboard, navigate to Access > Service Auth.
-
Go to the Service Tokens tab.
-
Click Create Service Token.
-
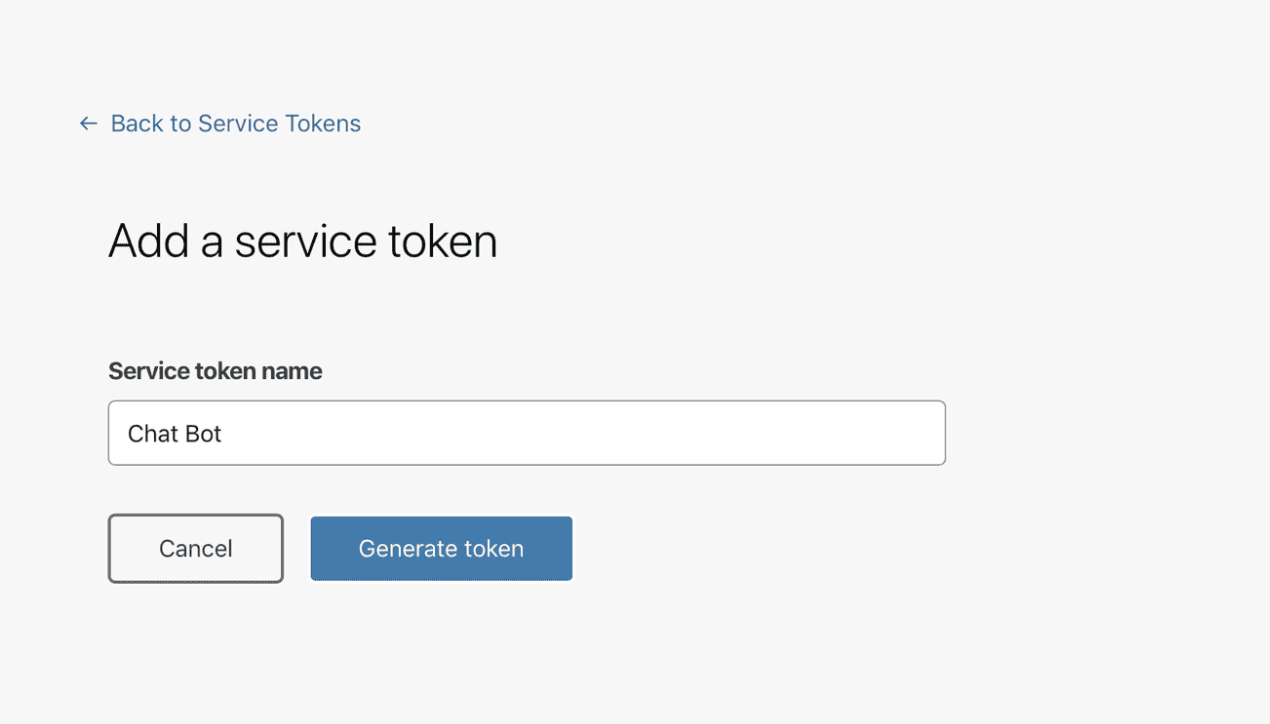
Next, name the service token.
The name allows you to easily identify events related to the token in the logs and to revoke the token individually.
-
Click Generate token.
The next page will display the generated
Client IDandClient Secretfor the service token. -
In the next page, copy the
Client Secret.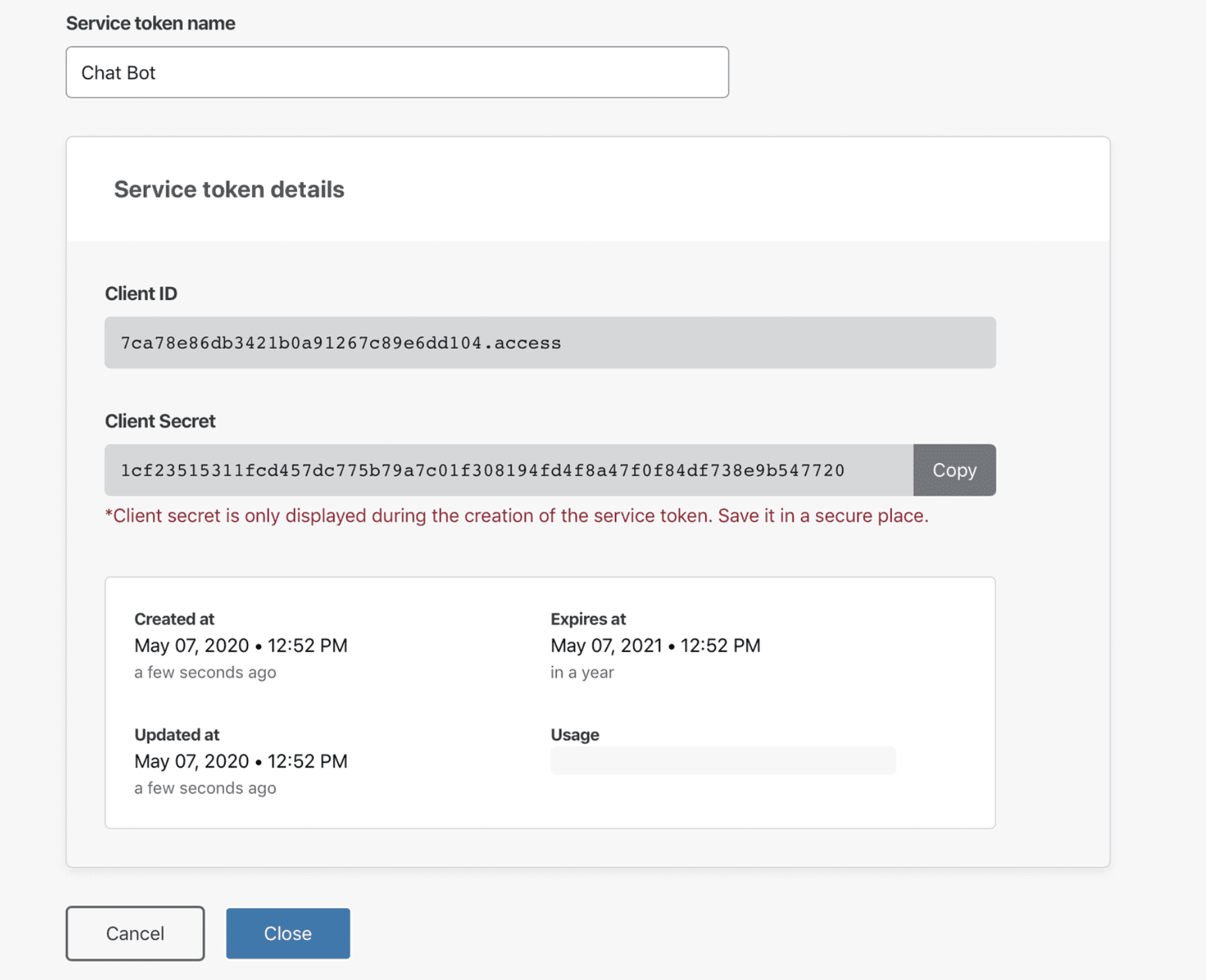
-
Click Close.
You can now use the service token when you create
service auth policies
. When creating these policies, use the Service Auth action to ensure that the identity provider login screen is not required for end users.
Connect your service to Access
Access expects both values as headers in any request sent to the applications behind Access. Add the following to the headers of any requests and name them as follows:
CF-Access-Client-Id: <Client ID>
CF-Access-Client-Secret: <Client Secret>
When a request is made to an application behind our network, the request will submit them both to Access. If the service token is valid, Access generates a JWT scoped to the application. All subsequent requests with that JWT will succeed until the expiration of that JWT.
Renew service tokens
By default, service tokens expire one year after creation. You can extend a token’s lifecycle by navigating to the Service Tokens tab and clicking the Refresh button for the token you want to renew.
The Refresh operation will extend the token’s lifetime by one year from the date of the refresh.
Revoke service tokens
By default, Access service tokens expire one year after they are created. If you need to revoke access earlier, simply delete the token.
To revoke a service token immediately:
-
On the Teams dashboard, navigate to Access > Service Auth > Service Tokens.
-
Click Delete for the token you need to revoke and delete.
When revoking service tokens, keep in mind:
- Services that rely on a deleted service token can no longer reach your application.
- Clicking Revoke Existing Tokens when editing a policy in the Edit Access Policy dialog revokes existing sessions but does not revoke access.
As long as the Client ID and Client Secret are still valid, they can be exchanged for a new token on the next request. To revoke access, you must delete the service token.
Set a token expiration alert
Service tokens have a default expiration of 12 months from when they are first created. An alert can be configured to notify a week before a service token expires to allow an administrator to invoke a token refresh.
To configure a service token expiration alert:
-
Navigate to the Cloudflare dashboard.
-
Select the Notifications tab.
-
Click Create.
-
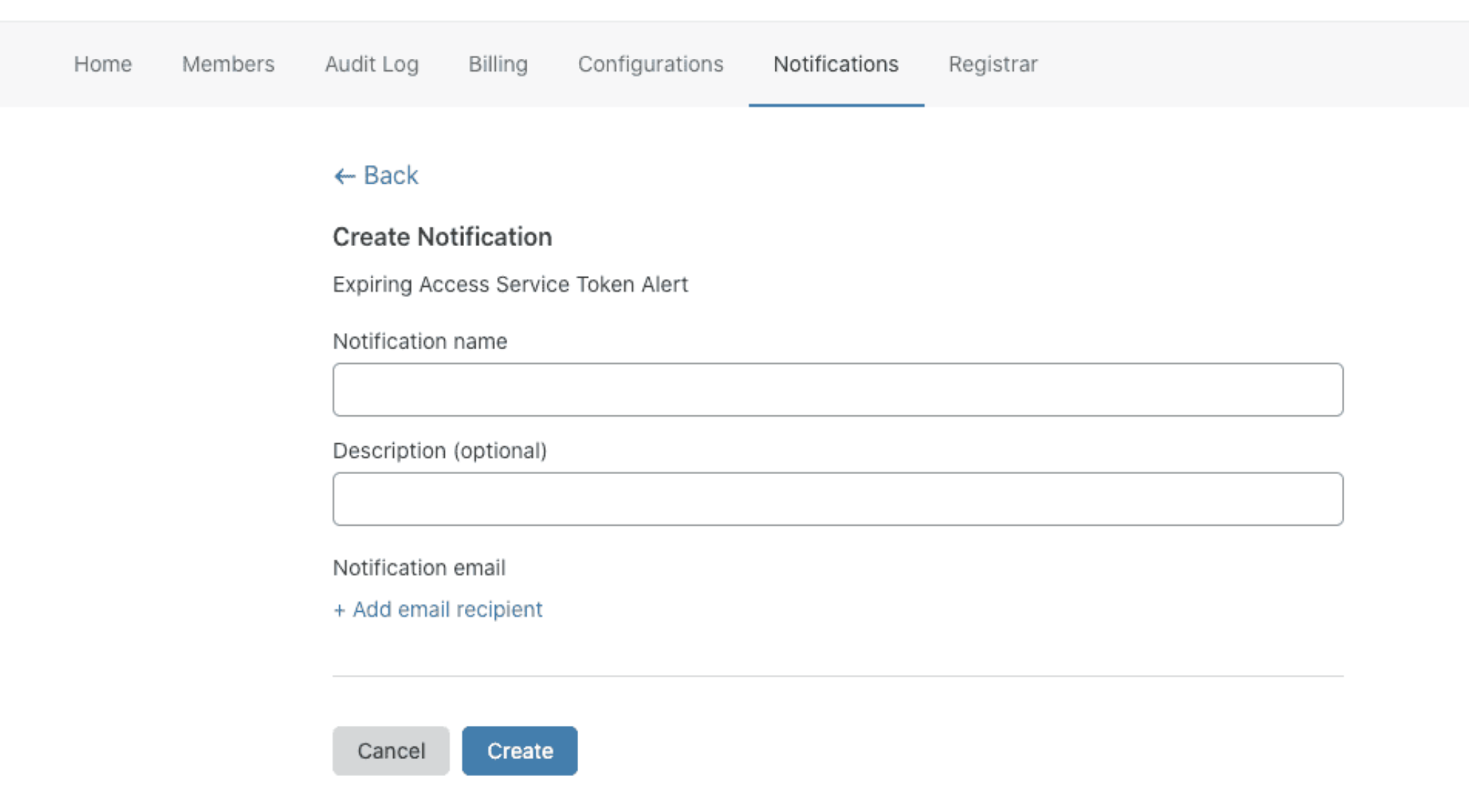
Select the Event Type “Expiring Access Service Token”.
-
Enter a name for your alert, and an optional description.
-
If you’d like to add other recipients for the notification email, click +Add email recipient.
-
Click Create.
Your alert has now been set, and is now visible in the Notifications tab of the Cloudflare dashboard.