Okta
You can integrate Okta with Cloudflare Access to allow users to reach applications protected by Access with their Okta account.
- In your Okta dashboard, click Admin.
- Select the Applications tab in the Admin dashboard.
- Click Create App Integration in the top right corner.
- In the pop-up dialog, select OpenID Connect.
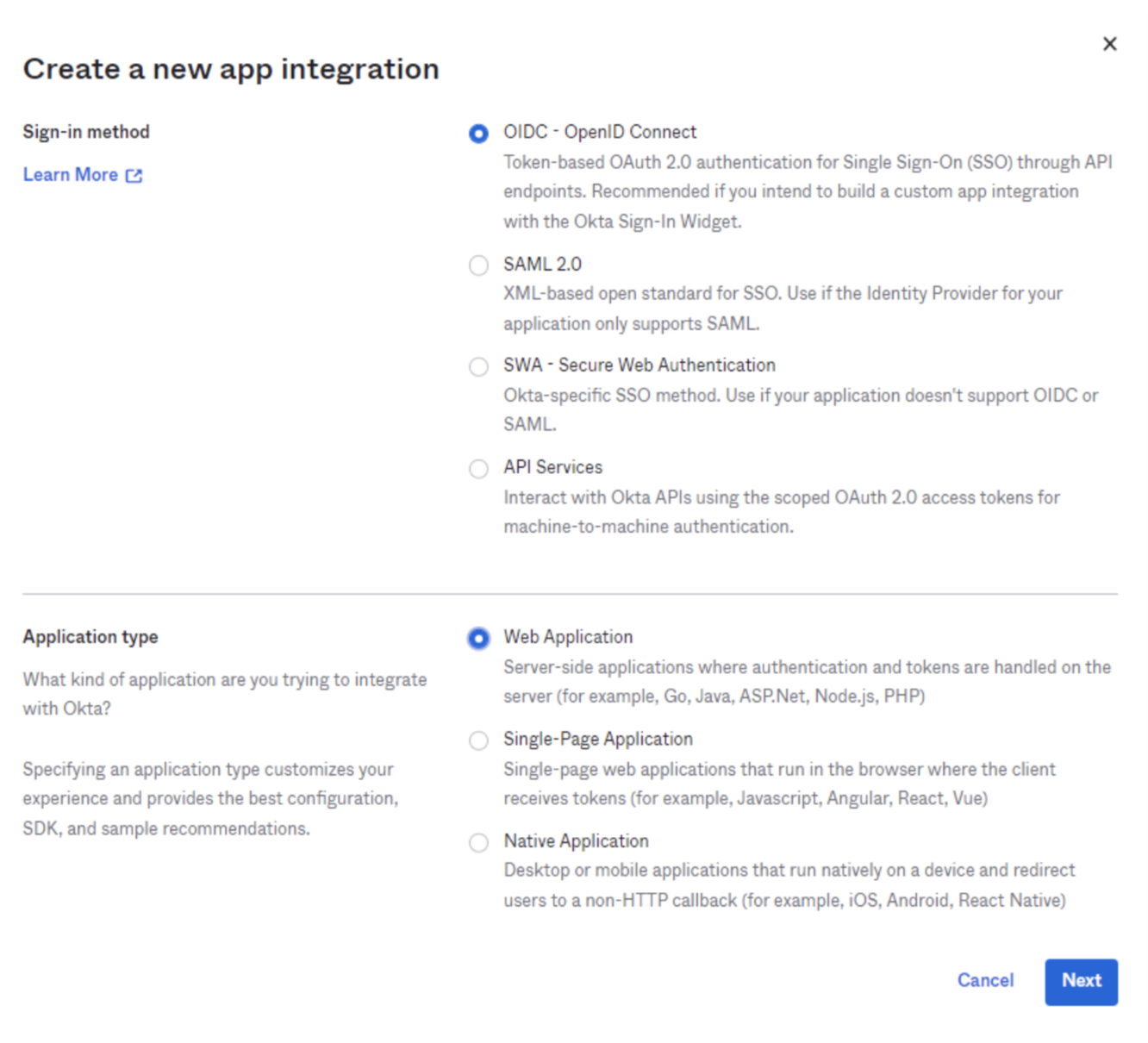
-
Choose
Web Applicationas the Application type and click Next. -
Enter any name for the application. In the Login redirect URIs field, input your team domain followed by this callback at the end of the path:
/cdn-cgi/access/callback. For example:https://<your-team-name>.cloudflareaccess.com/cdn-cgi/access/callback -
Specify an assignment. Any value can be selected based on the desired behavior.
-
Click Save.
-
From the application view, navigate to the Sign On tab.
-
Scroll down to the OpenID ConnectID Token.
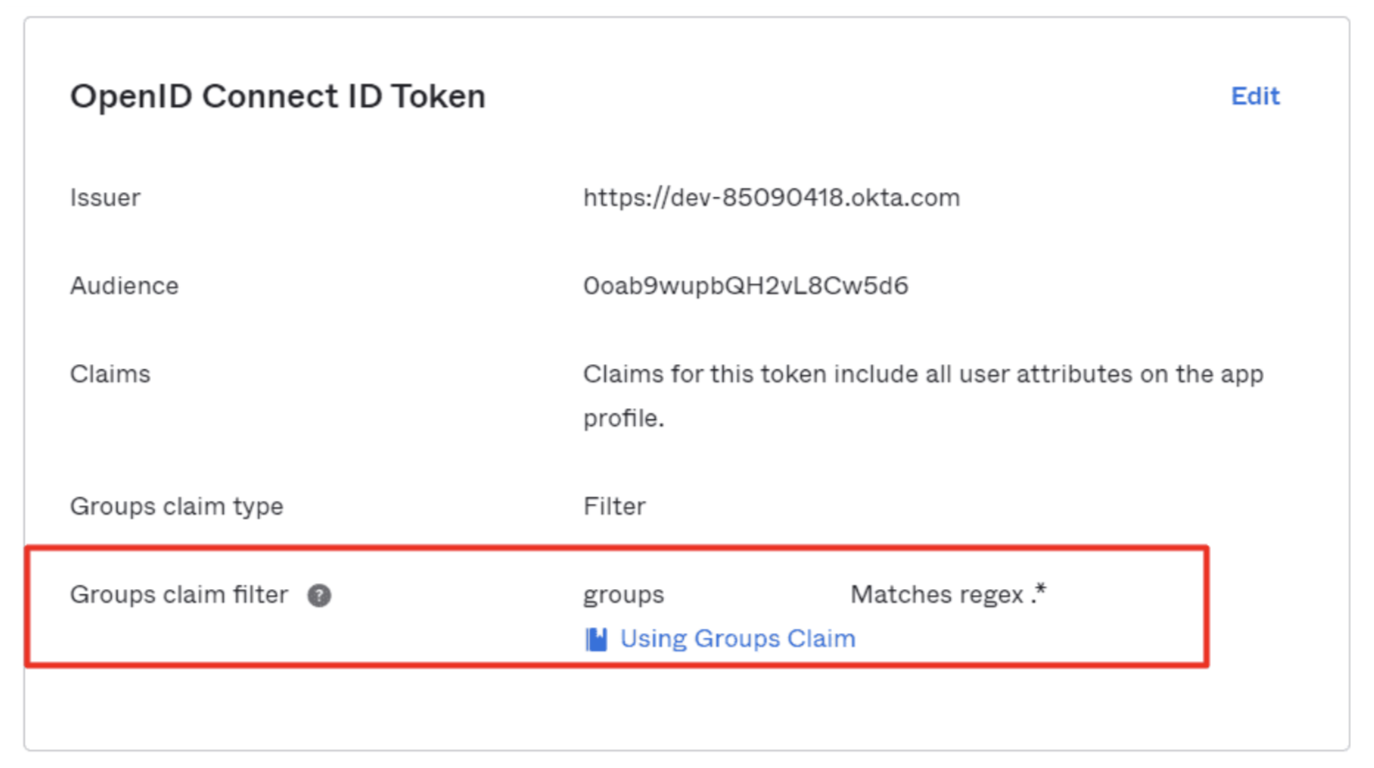
-
Click Edit and set the Groups claim filter to Matches regex and the value
.*. -
Return to the General tab. Scroll down to find your credentials, and copy the ID and secret.
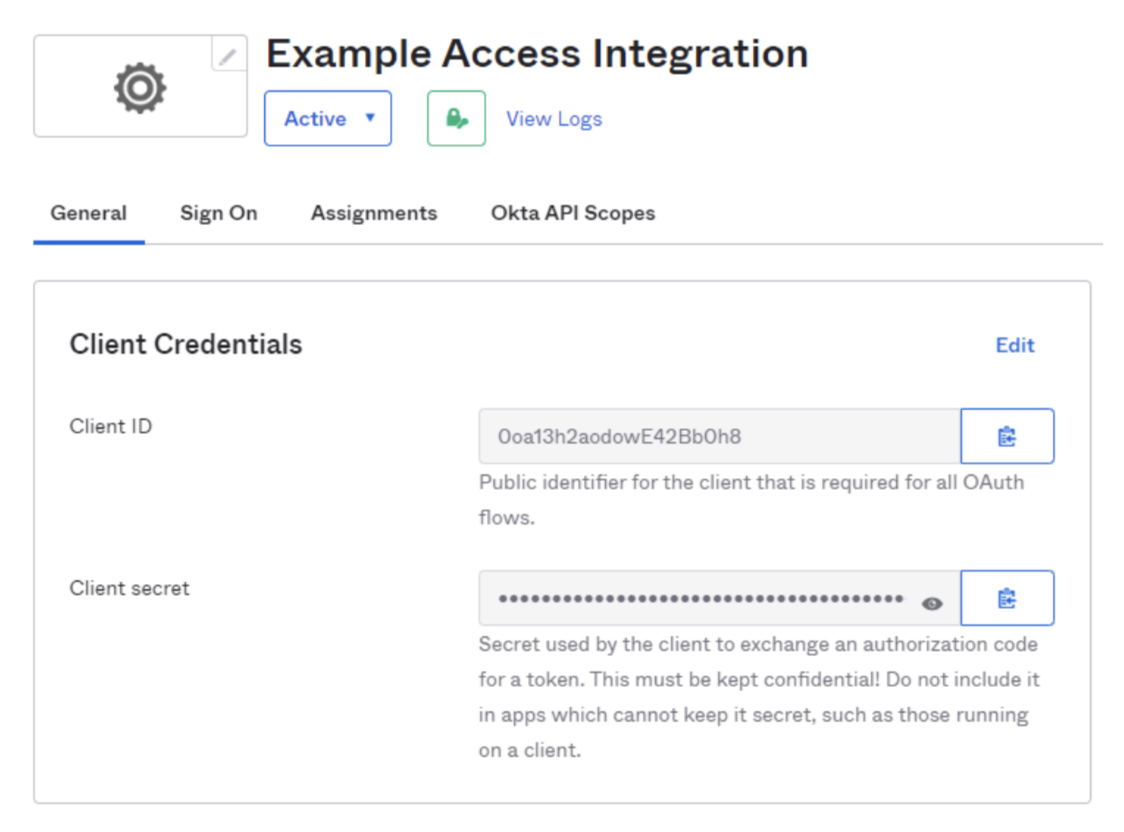
-
On the Zero Trust dashboard, navigate to Settings > Authentication.
-
Under Login methods, click Add new.
-
Select Okta as your identity provider.
-
Input the ID, secret, and the Okta account URL.
-
(optional) Create an Okta API token and enter it in the Zero Trust dashboard (the token can be read-only). This will prevent your Okta groups from failing if you have more than 100 groups.
-
Click Save.
To test that your connection is working, navigate to Settings > Authentication > Login methods and click Test next to Okta.
Example API Configuration
{
"config": {
"client_id": "<your client id>",
"client_secret": "<your client secret>",
"okta_account": "https://dev-abc123.oktapreview.com"
},
"type": "okta",
"name": "my example idp"
}