About Cloudflare Firewall Rules
Flexibility and control
Cloudflare Firewall Rules is a flexible and intuitive framework for filtering HTTP requests. It gives you fine-grained control over which requests reach your applications.
Firewall Rules allows you to create rules combining several conditions. For example, you can create a single firewall rule that blocks traffic to a URI when the request comes from a particular IP and the user-agent matches a specific string or a pattern. Once you are satisfied with the rule, you can deploy it yourself, immediately.
Fundamentally, Firewall Rules gives you the power to proactively inspect incoming site traffic and automatically respond to threats. You define expressions that tell Cloudflare what to look for and specify the appropriate action to take when those criteria are satisfied.
To write firewall rule expressions, use the Rules language, a powerful expression language inspired in the Wireshark Display Filter language. Even though Cloudflare Firewall Rules is not based on the Ruleset Engine , firewall rule expressions use the same syntax of the Cloudflare Rules language.
For more information on rule expressions and the available operators, fields, and functions, refer to Rules language .
Working with firewall rules
To configure firewall rules from the Cloudflare dashboard, use the Firewall rules tab in Security > WAF. For more, refer to Manage rules in the Cloudflare dashboard .
To configure firewall rules with the Cloudflare API, use the Firewall Rules API. Use the Cloudflare Filters API to manage expressions. For more information, refer to Manage rules via the APIs .
You can also manage firewall rules through Terraform. For more, refer to Getting Started with Terraform.
Firewall rules tab
The Rules List gives you a snapshot of recent activity and allows you to manage firewall rules in a single convenient location.
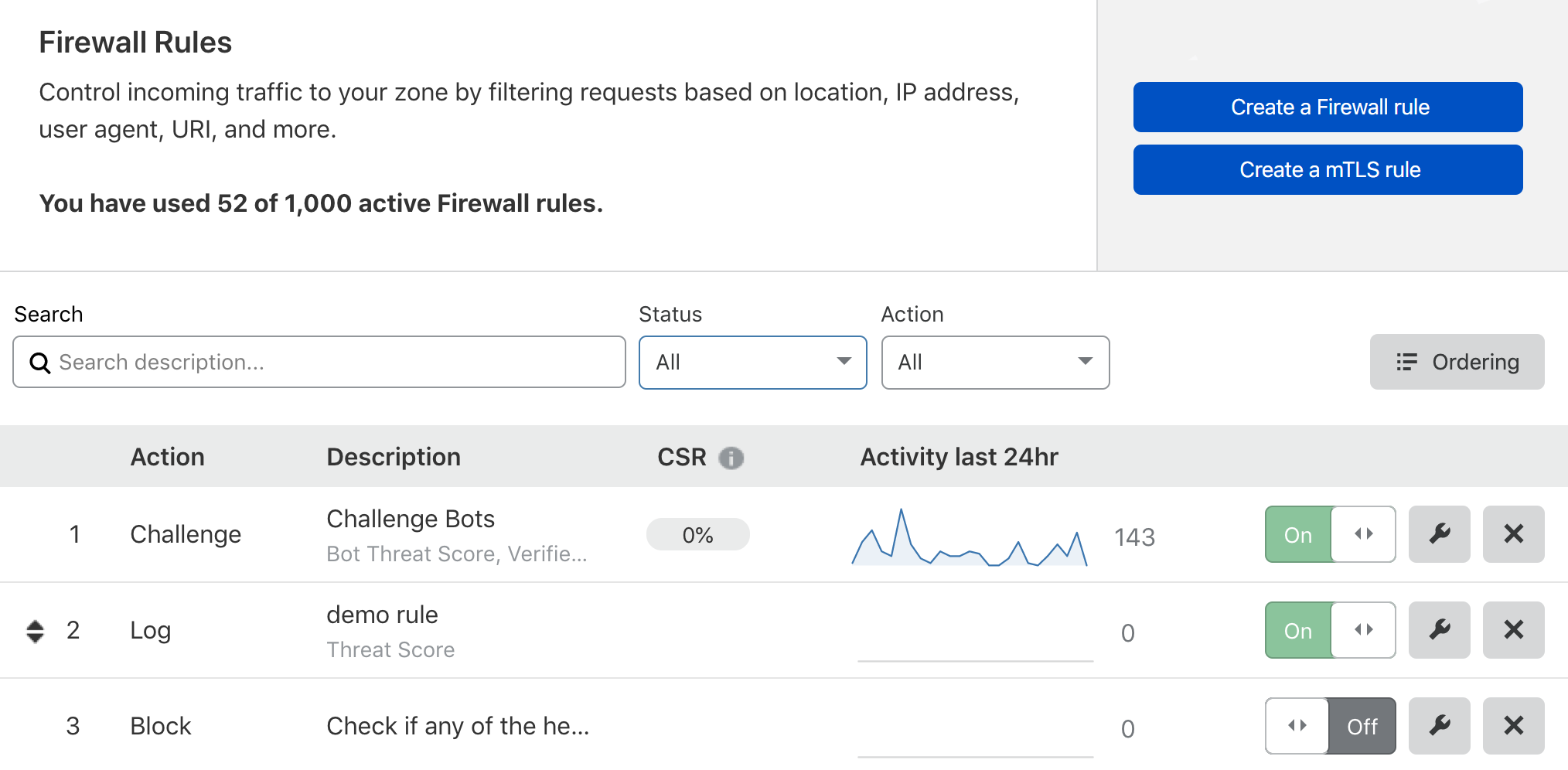
Challenge Solve Rate (CSR)
The Rules List displays each rule’s CSR (Challenge Solve Rate), which is the percentage of issued challenges that were solved. This metric applies to rules configured with Legacy CAPTCHA or JS Challenge actions, and it is calculated as follows:
CSR = number of challenges solved / number of challenges issued
Hover over the CSR to reveal the number of issued and solved CAPTCHA challenges:
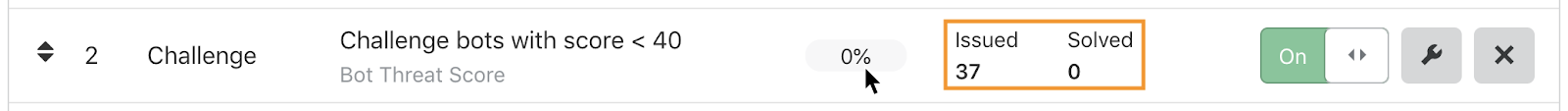
A low CSR means that Cloudflare is issuing a low number of CAPTCHA challenges to actual humans, since these are the solved challenges.
You should aim for a low Challenge Solve Rate. Review the CSR of your CAPTCHA rules periodically and adjust them if necessary:
- If the rate is higher than expected, for example regarding a Bot Management rule, consider relaxing the rule criteria so that you issue fewer challenges to human visitors.
- If the rate is 0%, no CAPTCHA challenges are being solved. This means that you have no human visitors whose requests match the rule filter. Consider changing the rule action to Block.
Firewall Rules APIs
Power users, particularly those who develop large numbers of firewall rules, can use the Cloudflare API to programmatically manage firewall rules. Refer to Manage rules via the API for more information.
Entitlements
Cloudflare Firewall Rules is available to all customers. However, the number of active firewall rules you can have and support for the Log action and regular expressions depend on your Cloudflare plan.
This table outlines the Firewall Rules features and entitlements available with each customer plan:
| Cloudflare plan | ||||
| Feature | Free | Pro | Business | Enterprise |
| Active rules | 5 | 20 | 100 | 1000 |
| Supported actions | All except Log | All except Log | All except Log | All |
| Regular expression support | No | No | Yes | Yes |
| Number of IP Lists | 1 | 10 | 10 | 10 |
Get started
Unless you are already an advanced user, refer to Expressions and Actions to learn more about the basic elements of firewall rules.
To get started building your own firewall rules, refer to Manage firewall rules in the dashboard .
Those eager to dive straight into the technical details can refer to these topics: